3 minutes
Hackthebox Paper
Paper is a machine with the Linux OS and is classified as easy. This machine has been retired and replaced by a new machine called Trick.
Machine IP: 10.10.11.143
As usual, I performed a service and port scan using Nmap and got the following result:
Nmap scan report for paper.htb (10.10.11.143)
Host is up (0.11s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
There was a suspicious header on port 80 that I suspected might be a domain for the machine.
me@nowhere:~/htb/paper$ curl -I 10.10.11.143
HTTP/1.1 403 Forbidden
Date: Mon, 20 Jun 2022 08:29:09 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Content-Type: text/html; charset=UTF-8
I added the domain office.paper to the hosts file on my local machine. When I accessed http://office.paper/, there was a website running a WordPress CMS, so I conducted a scan using WPScan.
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
| Found By: Rss Generator (Passive Detection)
| - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
| - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
Since I saw that the WordPress version was 5.2.3, which is quite old, I searched for vulnerabilities and found that this version had a flaw allowing the reading of unpublished drafts by accessing http://office.paper/?static=1. (CVE-2019–17671).
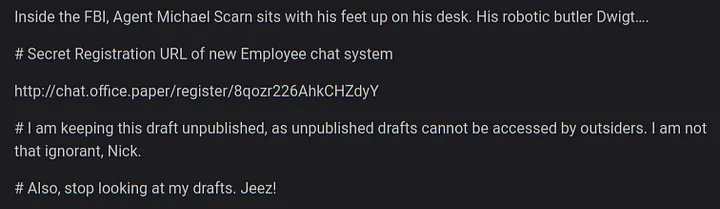
Here, I found a new subdomain, chat.office.paper, and a URL for employee registration. I added this subdomain to my hosts file and accessed the provided URL.
After registering, I opened the general channel and sent a direct message to the bot Recyclops. Recyclops has commands for reading files (file), listing directories (list), and showing the time (time). There is also a hidden command, run, for executing commands, which I found by reading the Hubot source code. This command can be used for a reverse shell, but there is an easier method: reading the password of the user dwight stored in ../hubot/.env.

I logged into the SSH service using the username dwight and password Queenofblad3s!23 and retrieved the user.txt file.
[dwight@paper ~]$ id
uid=1004(dwight) gid=1004(dwight) groups=1004(dwight)
[dwight@paper ~]$ cat user.txt
96b5646a650f6[redacted]
I performed enumeration using LinPeas.sh and found that the machine was vulnerable to CVE-2021–3560.
I saved the exploit file to my local machine, transferred it to the Paper machine, and executed it using Python to gain a shell as root.
[root@paper tmp]# id
uid=0(root) gid=0(root) groups=0(root)
[root@paper tmp]# cat /root/root.txt
c8cd82908786116[redacted]
Rooted!